Salesforce Tutorial# 6: Salesforce Security Model and Overview
Data Security is a big challenge for any cloud platform. Salesforce Security Model provides security at different levels like Object level, Field level, Record Level, etc to make consumer’s data more secured. In this article, we will get an overview of the Security Model in Salesforce.
Salesforce limits data exposure to maintain security on various levels. Salesforce makes authentication of users to avoid data access by unauthorized users.
For user authentication, salesforce builds a combination of authentication methods which are suitable for organizational need as well as customers need. It may include Password, Two-Factor Authentication, Network-based security, Session security, etc.
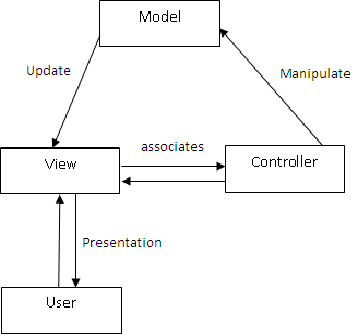
Salesforce Security Model:
Salesforce declares various sharing rules for different levels. Following are the few sharing rules with their default sharing access.
- Account sharing rules : Accounts and their associated contacts, opportunities, cases, and optionally, contacts and orders
- Account territory sharing rules : This can be shared with Accounts and their associated cases, contracts, contacts, and opportunities
- Campaign sharing rules : Individual campaign records
- User sharing rules : Individual user record
- Opportunity sharing rules : Individual opportunities and their associated accounts
Apart from these sharing rules, we can have criteria-based sharing rules which determine whom to share records based on field values in records. You can create criteria-based sharing rules for opportunities, cases, contacts, leads, campaigns, and custom objects, accounts. We can create up to 50 criteria-based sharing rules per object.
Object Level Security:
To maintain object level security salesforce allows various access levels of an object to the user.
| Permissions | Description |
| Read | User can only read data (view data) |
| Edit | User can edit data (read + write data) |
| Create | User can read and Create data |
| Delete | User can read, edit and delete data |
| Modify All | Users can view all records associated with an object, ( sharing settings are ignored). |
| View All | Users can read, edit, delete, transfer, and approve all records associated with this object, (sharing settings are ignored). |
Record Level Securities
Salesforce allows you to share your records with others setting permissions like Full access, Read/Write, Read-only, and private access. In Full access, users can edit, delete, transfer, and view records. Users can even extend the sharing of access to other users. In Read/Write access users can perform only Read or write operations on record. In read only mode users can only view the record. In private mode, the record is not shared with any other user.
- Describe OWD (Organization-Wide Default) : Organization-wide sharing settings specify the default level of access to records and can be set separately for contacts, , contacts, accounts, activities, assets, campaigns, cases, leads, opportunities, orders, and custom objects.
- Record sharing using Roll-Hierarchy:
We can define a user role hierarchy that can be used with sharing settings to determine the levels of access that users have for the data. These roles within the hierarchy affect access to key components such as records and reports.
Field Level Securities
To set field-level security we define field permissions. These permissions specify the access level for each field in an object. This feature is available in salesforce classic and Lightning Experience.
Steps to define field-level security
- From the management settings for the field’s object, go to the area of the field.
- Select the field.
- Click on View Field Accessibility.
- Specify the field’s access level.
There are different access levels for field data.
| Access Level | Enabled Settings in Permission Sets and Enhanced Profile User Interface | Enabled Settings in Original Profile and Field-Level Security Interfaces |
| Users can read and edit the field. | Read and Edit | Visible |
| Users can read but not edit the field. | Read | Visible and Read-Only |
| Users can’t read or edit the field. | None | None |
Ref: https://developer.salesforce.com/docs/atlas.en-us.securityImplGuide.meta/securityImplGuide/users_profiles_field_perms.htm
Field Properties:
Apart from the access level of the field, Salesforce allows field-level security by setting some field properties as follows:
- Unique property: If this property is checked then salesforce prevents that field from duplicates.
- External Id (Considered in Data Management): An external ID field contains record identifiers from a system outside of Salesforce. For each object in salesforce can have custom fields, we can set up auto-number, email, number, or text fields as external IDs.
- Required property: This property makes the field required everywhere in Salesforce. This property is not available for external objects.
Tutorial Index
- Introduction to Cloud Computing (Salesforce.com and Force.com)
- Overview of Database Concepts (Salesforce.com)
- Introduction to Force.com
- Building Salesforce Custom App and Objects
- Object Relationships and Formula Field in Salesforce
- Salesforce Security Model and Overview
- Automation in Salesforce
- Approval Process in Salesforce
- Introduction to SOQL and SOSL
- Introduction to Apex
- Salesforce Data Management
- Visualforce MVC Architecture on Cloud
- Salesforce Reports and Dashboards
- Building a Visualforce (Custom) Page for the Salesforce App
- Salesforce Sandbox and Overview of Force.com capabilities
- Learning Apex and Deployment Tools